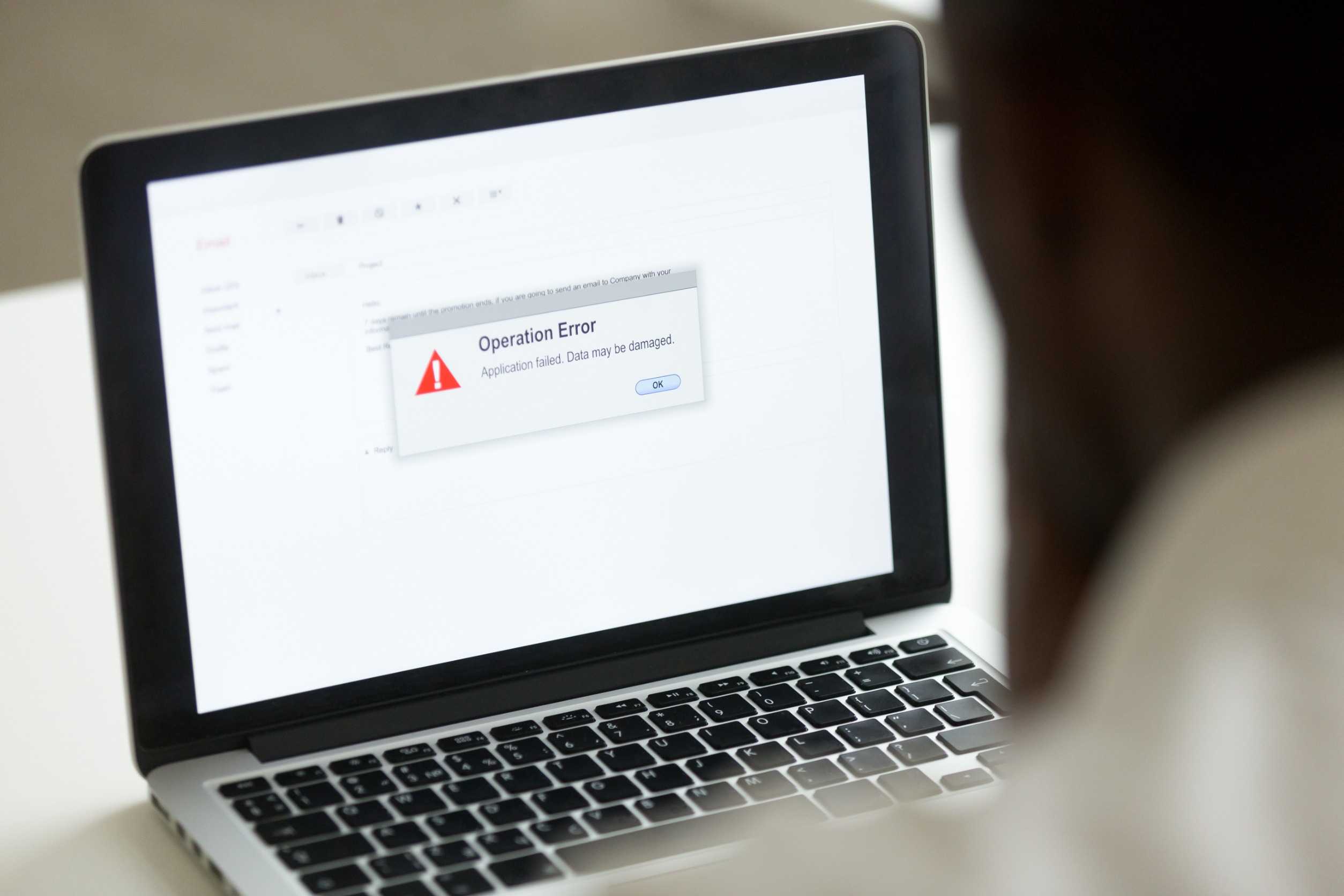
The recent CrowdStrike outage in 2024 underscored the vulnerabilities inherent in even the most robust systems, serving as a stark reminder of the importance of securing critical points of failure and dependencies

Articles by Calvin Thain
The Dangers of AI Tools and How to Protect Your Data
Artificial Intelligence (AI) tools have become ubiquitous, offering immense benefits in various fields such as healthcare, finance, and everyday consumer applications. However, the rise of AI also brings with it a host of potential dangers that must be carefully managed
MDM vs. MAM: Comparing & Understanding Key Differences
Businesses increasingly rely on mobile technology to enhance productivity and streamline operations. However, managing and securing these devices and the applications they run is a significant challenge.
Ways to Use Microsoft CoPilot AI to Help Your Small Business
Microsoft Copilot AI is an AI-powered assistant built into Microsoft 365 applications, designed to boost productivity and streamline tasks. In this article, we’ll explore practical ways small businesses can use Microsoft Copilot AI in their day-to-day operations.
What is Incognito Mode & What Does It Do? Is it Actually Private?
Incognito Mode, a Google Chrome feature, seeks to address online privacy concerns for internet users. But what is incognito mode?…and what does it actually do?
What is the Best Multifactor Authentication Type? – A Guide to MFA
Safeguarding sensitive information is a pressing concern for individuals and organizations alike. With cyber threats on the rise, traditional authentication methods are proving insufficient in protecting against unauthorized access. Multifactor authentication (MFA) offers an extra layer of security beyond passwords.
Your Apple device might be vulnerable To The GoFetch Vulnerability!
A significant flaw in Apple’s M-series chips, called the GoFetch vulnerability, has been found. In this post, we will go over what the vulnerability is, how it works, the implications it may hold for Apple users, and what you can do about it. What is the GoFetch...
Dropbox for Business Security: 14 Ways to Make Dropbox Safer
Hardening cloud solutions like Dropbox for business security is critical. It’s essential to implement robust security measures to safeguard confidential information. Review our Dropbox security checklist to learn how to make Dropbox more secure within your organization.
Do you use an iPhone or any other Apple device? If so, this message is for you.
Apple devices are at risk due to a vulnerability that has huge potential for allowing a data breach. This zero-day vulnerability is putting millions of Apple devices at risk, including iPhones, iPads, Macs, Watches, and TVs. Quick Points Risk: High. Attackers can...
Google Workspace Security Best Practices Checklist for 2024 (formerly GSuite)
As we enter 2024, the importance of securing data and communications in the digital workspace is paramount. With remote work and digital collaboration at the forefront, Google Workspace plays a pivotal role for businesses globally.
Advancing Security: Trust Level 2 Attained!
We are thrilled to announce a significant milestone in our ongoing commitment to fortifying digital defenses – IntegriCom has achieved Trust Level 2 accreditation from Galactic Advisors.
Hardening Microsoft 365: Security Best Practices Checklist
Safeguarding sensitive information is non-negotiable, especially for organizations relying on Microsoft 365 (formerly Office 365).