Table of Contents
Introduction
As we enter 2024, the importance of securing data and communications in the digital workspace is paramount. With remote work and digital collaboration at the forefront, Google Workspace plays a pivotal role for businesses globally. In this article, we introduce our practical Google Workspace Security Best Practices Checklist for 2024. Learn essential steps to enhance your organization’s digital security within the Google Workspace environment (formerly GSuite).
Is Google Workspace Secure?
While Google Workspace provides a good foundation for collaboration and productivity, it is essential to fully utilize both built-in features with additional security best practices and in some cases third-party offerings. The dynamic nature of the cybersecurity landscape demands a proactive approach to stay ahead of emerging threats. Educating users, implementing data loss prevention measures, employing multi-factor authentication, ensuring endpoint security, and conducting regular security audits are crucial steps. Tailoring security measures to meet industry-specific compliance requirements and customizing them according to organizational needs are also vital. By embracing these practices, organizations can fortify their defenses, mitigate risks, and maintain a robust security posture beyond the capabilities offered by Google Workspace default settings alone.
Why is it important to secure my Google Workspace?
Securing Google Workspace is essential to prevent a range of potential threats and mitigate risks that could have severe consequences for organizations. Without proper security measures, the platform is vulnerable to data breaches, phishing attacks, data loss, malware, and ransomware, which can compromise sensitive information and disrupt business operations. Unsecured accounts may lead to identity theft, non-compliance with regulations, financial losses, and reputation damage. Intellectual property theft is also a concern, posing a threat to an organization’s competitive edge.
How do I secure my Google Workspace?
Part 1: Apps
Google Workspace Apps, including Gmail, Google Drive, and Google Calendar, are integral to organizational collaboration and productivity. Securing these apps is crucial to prevent unauthorized access, data breaches, and phishing attacks. For example, securing Gmail helps thwart phishing attempts, while robust measures for Google Drive safeguard shared documents, and Calendar security ensures the protection of scheduling information. The significance of securing Google Workspace Apps lies in preserving the integrity, confidentiality, and availability of organizational data and communications, addressing diverse cybersecurity threats that may target these essential tools.
Don’t allow users to install and run apps from the Marketplace
 Allowing users to install apps from the Google Play Store poses risks such as malware, data privacy concerns, and unreliable or counterfeit apps. Malicious apps may compromise security and privacy, while poorly designed or fake apps can impact device performance. Users should employ security software, review permissions, check reviews, and keep software updated to mitigate these risks and exercise caution with apps from unknown developers. App marketplaces have security measures, but user vigilance is essential for protecting devices and personal information.
Allowing users to install apps from the Google Play Store poses risks such as malware, data privacy concerns, and unreliable or counterfeit apps. Malicious apps may compromise security and privacy, while poorly designed or fake apps can impact device performance. Users should employ security software, review permissions, check reviews, and keep software updated to mitigate these risks and exercise caution with apps from unknown developers. App marketplaces have security measures, but user vigilance is essential for protecting devices and personal information.
Review Domain Installed Apps for Suspicious Apps
To secure Google Workspace from potentially harmful apps, regularly review and audit installed apps, checking for legitimate sources, appropriate permissions, and user feedback. Implement app whitelisting/allowlists, monitor app behavior, utilize security tools, and educate users on app security to create a comprehensive defense strategy against unauthorized or malicious applications, ensuring the integrity and security of organizational data and communications.
Check Mail Forwarding Rules
 Regularly reviewing mail forwarding rules is crucial for cybersecurity as it helps prevent data leakage, unauthorized access, and phishing attacks. This practice ensures the integrity of organizational communication, aids in compliance with data protection regulations, and detects anomalies or security incidents promptly, contributing to a proactive defense against evolving cyber threats and maintaining trust among stakeholders.
Regularly reviewing mail forwarding rules is crucial for cybersecurity as it helps prevent data leakage, unauthorized access, and phishing attacks. This practice ensures the integrity of organizational communication, aids in compliance with data protection regulations, and detects anomalies or security incidents promptly, contributing to a proactive defense against evolving cyber threats and maintaining trust among stakeholders.
Do not use mail forwarding rules to external domains
Using mail forwarding rules to external domains poses security risks such as phishing, data leakage, and loss of control over sensitive information. Compliance concerns, legal implications, and the potential for reputational damage further underscore the need for caution, emphasizing the importance of robust security measures and careful consideration of the associated risks before implementing such rules.
Check DNS for SPF Record
When checking DNS for an SPF record, it’s crucial to confirm the existence and correct syntax of the record, ensuring that it authorizes legitimate mail servers and follows the specified policy qualifiers. Additionally, attention should be given to include mechanisms, IP address allowances, and consistency with DKIM and DMARC records to enhance overall email authentication and security. Regular validation using SPF testing tools helps identify and address potential issues.
You can find additional information and instructions in the Google help article below.
Google help article: Add your SPF record at your domain provider
Part 2: Security
In fortifying the security of Google Workspace, several key measures are essential to bolster cybersecurity resilience. Multi-Factor Authentication (MFA) stands as a fundamental layer, adding an extra level of protection beyond passwords and significantly reducing the risk of unauthorized access. Even if MFA is not enabled, enforcing a robust password policy acts as the first line of defense against potential vulnerabilities like brute-force attacks. User account recovery mechanisms provide a secure way for users to regain access, striking a balance between security and accessibility. Enrolling users in the Advanced Protection Program (APP) elevates protection against advanced threats, leveraging hardware security keys and restricting third-party app access. Additionally, disabling less secure apps, especially those using legacy authentication, is crucial to mitigating unauthorized access risks. Keeping abreast of updates and consulting cybersecurity professionals is essential for maintaining a robust security posture.
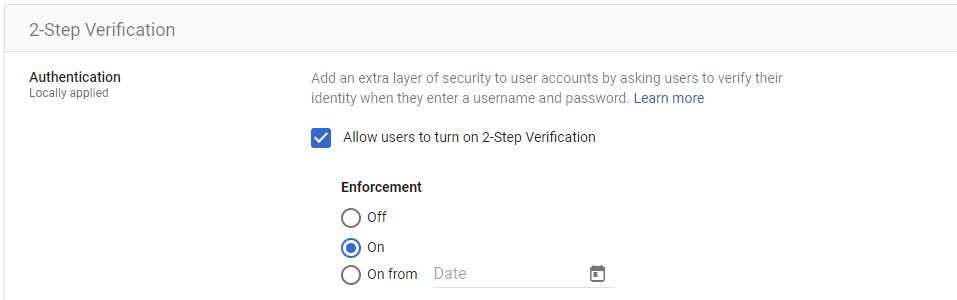
Enable 2FA for all users
 Multi-Factor Authentication (MFA) is crucial for security as it adds an extra layer of protection beyond just passwords, requiring users to verify their identity through multiple means, such as a mobile app or a biometric scan. This significantly reduces the risk of unauthorized access, even if login credentials are compromised, enhancing overall cybersecurity resilience.
Multi-Factor Authentication (MFA) is crucial for security as it adds an extra layer of protection beyond just passwords, requiring users to verify their identity through multiple means, such as a mobile app or a biometric scan. This significantly reduces the risk of unauthorized access, even if login credentials are compromised, enhancing overall cybersecurity resilience.
Enforce Password Policy if 2FA is not enabled
Enforcing a password policy is important even if Multi-Factor Authentication (MFA) is not enabled because strong and unique passwords act as the first line of defense against unauthorized access. A robust password policy helps mitigate risks associated with password-related vulnerabilities, such as brute-force attacks or password guessing, providing an additional layer of security before users can enable the enhanced protection offered by MFA.
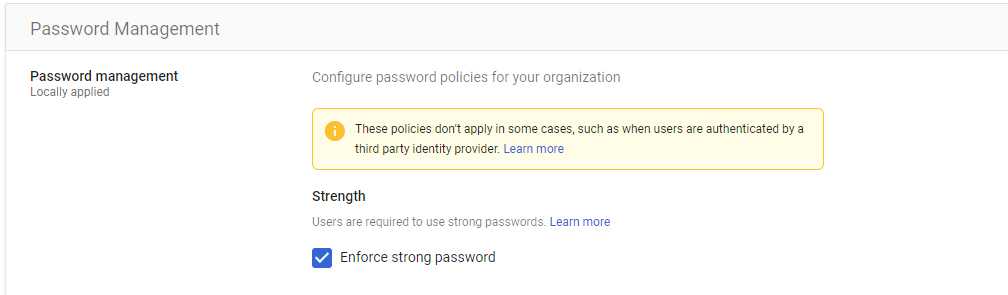
Enable user account recovery
Enabling user account recovery is beneficial for cybersecurity as it provides a secure and streamlined process for users to regain access to their accounts in case of a legitimate need, such as a forgotten password or a locked account. This helps prevent security risks associated with users resorting to insecure practices, such as using easily guessable passwords or creating multiple accounts, to cope with the fear of being locked out. A well-designed account recovery mechanism enhances user experience while maintaining a balance between security and accessibility.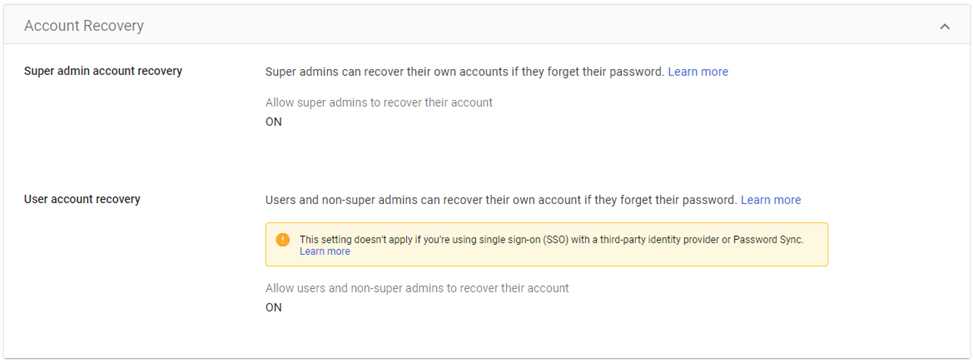
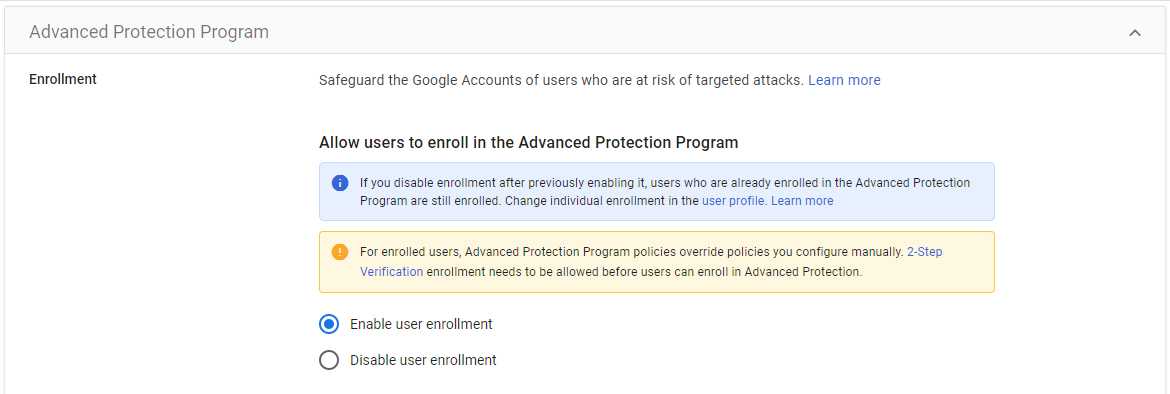
Enable user enrollment into Advanced Protection Program
Enabling user enrollment into the Advanced Protection Program (APP) is beneficial for cybersecurity as it offers an elevated level of protection against sophisticated phishing and account takeover attempts. By leveraging hardware security keys and restricting third-party app access, APP significantly enhances the security posture of user accounts, reducing the risk of unauthorized access and protecting sensitive information from advanced threats.
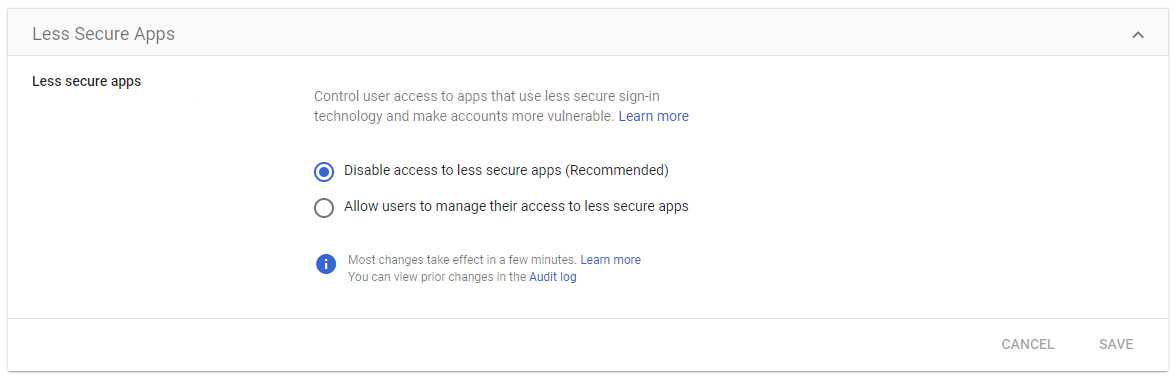
Disable Less Secure Apps (legacy authentication)
Disabling less secure apps, particularly those using legacy authentication methods, is essential for security as it helps mitigate the risk of unauthorized access and potential account compromise. Legacy authentication protocols often lack modern security features, making them susceptible to various attacks such as brute-force attempts or credential stuffing. Disabling these less secure apps ensures that only applications using more secure authentication methods have access, reducing the likelihood of successful cyberattacks and enhancing overall account protection.
Review High Severity Alerts
 Reviewing high severity alerts in cybersecurity is crucial as they signify potential serious threats to an organization’s systems and data. These alerts often indicate activities that could lead to data breaches or unauthorized access. Swift and thorough review enables timely mitigation, minimizing the impact of potential security incidents. Reviewing this weekly can be a great way to catch bad actors before they get too far. More often it is recommended but can be hard to do without automation or third-party tools.
Reviewing high severity alerts in cybersecurity is crucial as they signify potential serious threats to an organization’s systems and data. These alerts often indicate activities that could lead to data breaches or unauthorized access. Swift and thorough review enables timely mitigation, minimizing the impact of potential security incidents. Reviewing this weekly can be a great way to catch bad actors before they get too far. More often it is recommended but can be hard to do without automation or third-party tools.
Part 3: Account
This set of cybersecurity practices underscores the importance of limiting administrative roles according to the principle of least privilege. Additionally, designating multiple super admins, ensuring fewer than five super admins, customizing support messages cautiously, verifying time zones accurately, and incorporating a custom logo in Google Workspace collectively contribute to a resilient cybersecurity infrastructure. These measures address redundancy, attack surface reduction, control enhancement, and visual authentication, fostering a secure environment and fortifying defenses against evolving cyber threats.
Use limited administrative roles
 Limiting admin roles in alignment with the principle of least privilege is critical for cybersecurity. Adhering to least privilege ensures that users or systems have only the necessary access, reducing the risk of unauthorized access, privilege escalation, and potential misuse of administrative privileges. This practice enhances security by minimizing exposure to potential threats and mitigating the impact of security incidents.
Limiting admin roles in alignment with the principle of least privilege is critical for cybersecurity. Adhering to least privilege ensures that users or systems have only the necessary access, reducing the risk of unauthorized access, privilege escalation, and potential misuse of administrative privileges. This practice enhances security by minimizing exposure to potential threats and mitigating the impact of security incidents.
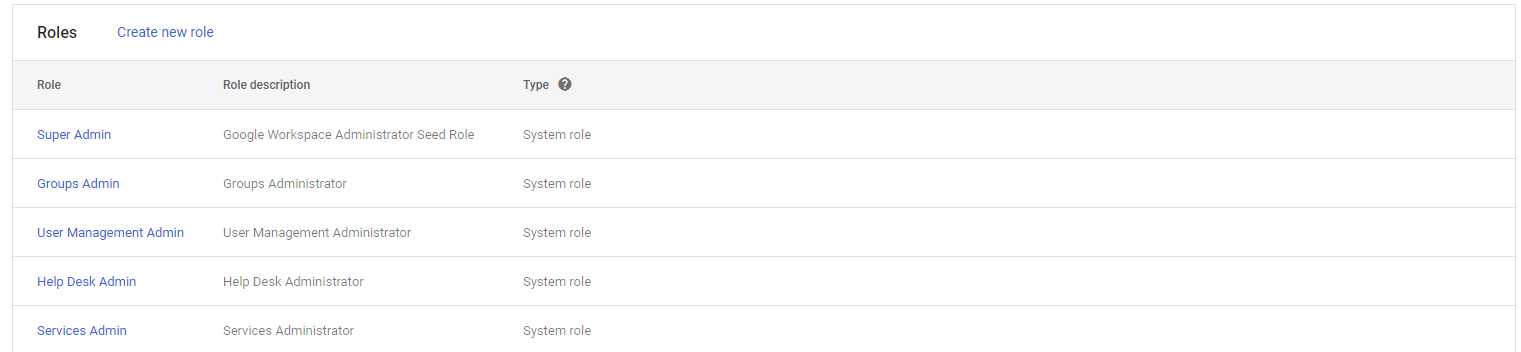
Designate more than one super admin
Designating more than one super admin is important for cybersecurity as it provides redundancy and ensures that critical administrative functions can still be performed even if one super admin account is compromised or inaccessible. This approach helps prevent a single point of failure, enhances resilience, and contributes to a more robust security posture for an organization’s administrative control.
Designate fewer than 5 Super Admins
Designating fewer than 5 super admins is crucial for cybersecurity by reducing the attack surface, enhancing control and accountability, and mitigating insider threats. This approach simplifies access management, prevents credential compromise, and enables quicker incident response, aligning with security best practices and contributing to a more resilient cybersecurity infrastructure. The number recommended is 2-5 depending on organization size.
Custom Logo
Having a custom logo in Google Workspace is important for cybersecurity as it acts as a visual deterrent against phishing attempts by making it more difficult for attackers to impersonate the organization. The logo ensures brand consistency, aiding users in recognizing legitimate communications and fostering a sense of trust in digital interactions. Incorporating the logo into phishing awareness training further strengthens its role as a key visual authentication element, empowering users to identify and mitigate social engineering threats.
Part 4: Rules & Alerts
Enabling alerts for user-granted admin privileges and user suspension due to suspicious activity in Google Workspace is imperative for cybersecurity. These measures provide real-time notifications, facilitating swift detection and response to potential security threats, including unauthorized access and data breaches. Proactive monitoring and documented incident responses contribute to a robust security posture, minimizing risks associated with administrative role changes and insider threats.
Alerts on for user granted admin privilege
Turning on alerts for user-granted admin privileges is essential for cybersecurity as it provides real-time notifications about significant changes in administrative roles, enabling quick detection and response to potential security threats. Alerting on user-granted admin privileges helps organizations monitor and review changes promptly, reducing the risk of unauthorized access, privilege escalation, or misuse of administrative roles. This proactive approach enhances overall security by allowing administrators to investigate and address potential security incidents promptly, minimizing the impact of any malicious activities.
Alerts on for User suspended due to suspicious activity
Enabling alerts for user suspension due to suspicious activity in Google Workspace is crucial for cybersecurity, providing real-time notifications that facilitate rapid threat detection and immediate incident response. This proactive measure helps prevent data breaches, minimizes insider threats, and safeguards the organization’s overall security posture. User suspension alerts also contribute to compliance efforts by providing a documented record of actions taken in response to security incidents, ensuring continuous monitoring, review, and refinement of security protocols.
Enhance Your Google Workspace Security with IntegriCom Managed IT Services
IntegriCom provides managed IT Services and can manage your Google digital workspace. Please contact us for a free evaluation of your workspace. We can provide a complete security assessment of your total environment and provide a remediation report and recommended support options.




