A significant flaw in Apple’s M-series chips, called the GoFetch vulnerability, has been found. In this post, we will go over what the vulnerability is, how it works, the implications it may hold for Apple users, and what you can do about it.
What is the GoFetch Vulnerability?
The GoFetch vulnerability is a newly discovered flaw embedded within Apple’s M-series chips. It allows attackers to extract secret keys from Macs during cryptographic operations, posing a significant threat to data security.
GoFetch Vulnerability: Implications for Users
The implications of the GoFetch vulnerability are serious. With attackers being able to extract secret keys from Macs, users’ sensitive information becomes vulnerable to theft. This could include passwords, financial data, or any other confidential information that relies on cryptographic protection.
What Can Users Do To Protect Themselves From The GoFetch Vulnerability?
Users must stay vigilant and take proactive measures to protect their data by updating software with the latest security patches. Additionally, users should be cautious when installing third-party applications, as they could inadvertently expose their systems to exploitation. We also recommend uninstalling applications that are no longer needed to reduce your attack surface.
How to check what CPU your Apple device has
If you have a Macbook Pro, Macbook Air, iPad, iMac, or a Mac mini from 2020 or later, you likely have an M-series chip in your device.
- Click the Apple logo at the top left of your screen
- Click “About This Mac”
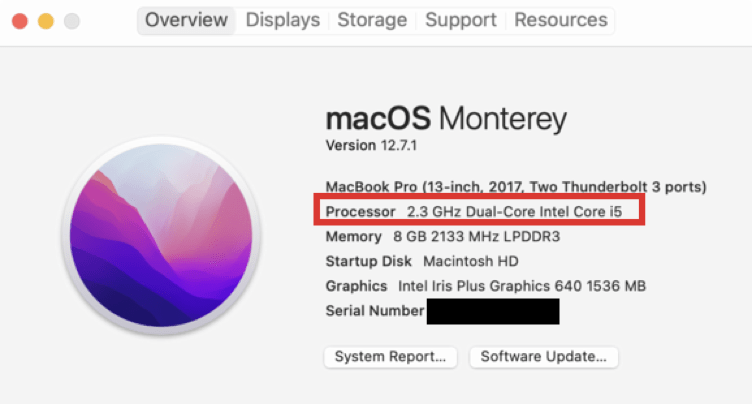
If you see an Apple M-Series chip in the highlighted box, you may be affected by this vulnerability.

If you see “Processor” and an Intel based CPU, you are not affected by this vulnerability.
How Does The GoFetch Vulnerability Work?
At the heart of the GoFetch vulnerability lies the chips’ data memory-dependent prefetcher, a hardware optimization designed to predict memory addresses of data likely to be accessed soon. While prefetchers are meant to enhance performance by reducing latency, they inadvertently create a side channel that attackers can exploit to obtain secret key material from cryptographic operations.
The prefetcher sometimes misinterprets secret data as memory addresses, allowing attackers to intercept and extract this information covertly. This “dereferencing” of “pointers” essentially leaks secret key material through a side channel, compromising the security of the system.
Unlike typical software vulnerabilities, GoFetch stems from the microarchitectural design of the silicon itself, making it challenging to patch directly. Instead, mitigations involve building defenses into cryptographic software, which could potentially degrade the performance of M-series chips, particularly on earlier generations like M1 and M2.


